Counter-Deception in Modern Espionage: Planning, Techniques and Challenges

In international security and espionage, counterintelligence (CI hereafter) serves as a line of defense against deceptive operations executed by foreign intelligence services. Counter-deception is a big aspect of modern CI, focusing on detecting and neutralizing deception strategies employed by adversaries. In this blog, I’d like to discuss the sophisticated techniques of counter-deception, primarily exploring their evolution, some of the challenges, and their application in historical contexts. These techniques have been refined over decades, adapting to the shifting landscapes of geopolitical strategies and technological advancements. Early techniques were often reactive, based on the analysis of enemy actions and intelligence reports. Today, they encompass a wide array of proactive strategies, including digital forensics, psychological profiling, and advanced data analytics. Counter-deception planning involves a systematic approach, comprising three interrelated concepts: detection of adversary deceptions, adoption of countermeasures to mitigate the impact of these deceptions which may include counter-deception operations, hereafter referred to as counter-stratagems and the coordination of these programs within a comprehensive counter-deception system. This systematized approach marks a departure from ad-hoc or ‘seat-of-the-pants’ counter-deception efforts, which typically consist of uncoordinated and sporadic attempts to detect and counteract foreign deception operations. These less structured efforts often rely on the intuition of overconfident intelligence analysts or on isolated analyses of specific elements of a deception package, such as camouflage designs or cryptologic intelligence. However, a true counter-deception system integrates these disparate efforts into a cohesive and effective framework, enhancing the ability to foresee, understand, and effectively neutralize adversarial deception strategies.

Soviet Counter-Deception in the 1960s
During the 1960 Olympics in Rome, the KGB executed comprehensive counter-deception operations to protect the Soviet delegation from Western intelligence activities, which they believed were being conducted under the guise of the Olympic Games. The KGB set up a counterintelligence task force within the Soviet sports delegation, which included KGB agents posing as delegates. This team was responsible for preventing any anti-Soviet provocations and also actively disrupted activities by the National Alliance of Russian Solidarists (NTS), which tried to spread anti-Soviet materials among the athletes. This included staging incidents to mislead the NTS and sowing discord among its members. Similar tactics could be used in modern conflicts where nations use large international events to conduct espionage or influence operations. It is not hard to imagine that in the ongoing conflict between Russia and Ukraine, both nations are deploying intelligence agents within their delegations to international forums or sports events to guard against or engage in influence operations.
Tactical Deployment of Disinformation
Soviet counterintelligence strategies extensively incorporated disinformation operations targeting foreign entities, serving multiple objectives including the compromise and exhaustion of enemy resources. A notable example involves the Estonian KGB's efforts to undermine exiled Estonian leaders through forged documents and disinformation. This operation included the creation of fictitious organizations whose purported communications were spread using agents and technical means to sow discord and discredit these leaders. Disinformation was strategically employed to mislead foreign experts and drain their resources. A case highlighted by Colonel V. Ryabov from the Sixth Department (Scientific and Technical Intelligence) of the FCD illustrates this tactic vividly. An American specialist known as "G" who planned to consult with a Soviet scientist "F" during his visit to Moscow was deliberately misled. Soviet counterintelligence advised "F" to leave the city, and during "G"'s stay, they intercepted a questionnaire intended for "F" that sought sensitive information on radio electronics. Although a direct opportunity for disinformation was missed in this instance, the potential to cause significant financial and developmental setbacks to American interests was clearly recognized by Ryabov. These practices not only sought to protect Soviet state secrets but also strategically drained the resources of their adversaries by leading them on wild goose chases or into dead ends. Such tactics of deception and resource exhaustion have historical echoes in modern conflicts, where similar strategies could be observed, for example, in the ongoing conflicts in Ukraine and between Israel and Palestine, where disinformation leads to misallocation of resources and strategic missteps on both sides. The KGB frequently in the 1960s used disinformation and the public exposure of compromising material to manipulate perceptions and control narratives. In 1960, they manipulated the visit of an American railway delegation by providing misleading information that exhausted the delegation's resources and diverted them from obtaining accurate data. In the Israel-Palestine conflict, similar strategies are being observed where both sides use media and online platforms to spread disinformation to influence international opinion and exhaust diplomatic efforts. Public exposure of compromising material is used to discredit political figures or movements, affecting their credibility and operational effectiveness. Similar disinformation tactics are being used by both sides in Russia and Ukraine to mislead each other about military capabilities and intentions. We see this online where both sides spread false information about troop movements or casualties to manipulate public perception and enemy planning. This is an obvious move.
Operational Games and Dangles
Dangle are the strategic deployment of double agents or informants who appear to defect or leak information. These agents provide controlled or misleading information to the enemy, influencing their decision-making processes and strategies. The Soviet practice of "operational games" involved feeding disinformation through double agents or controlled leaks to mislead and manipulate the enemy's intelligence efforts. A well-documented instance involves the KGB using agents posing as dissidents or defectors who provided false information to the CIA, leading to strategic misjudgments. In the Ukraine-Russia war, similar techniques could be employed by deploying double agents or misinformation to misdirect military tactics or misinform about troop movements and intentions. This can lead to strategic advantages where one side may prepare for a military action based on false intelligence, thereby weakening their actual defensive or offensive capabilities. We saw this in Soviet counterintelligence, under directives from figures like Oleg Gribanov, who systematically fed misleading information to the West. One such case involved an agent codenamed PILOT, who infiltrated U.S. intelligence in Latvia under the guise of a defector. This operation allowed the KGB not only to mislead U.S. intelligence about Soviet capabilities and intentions but also to control the channels of communication and infiltration used by U.S. agents in the Baltic states. During this time we also saw evidence of camouflage (maskirovka), which involves the physical or digital disguise of critical infrastructures, military bases, or other significant sites to prevent them from being identified or targeted by the enemy. This technique also includes creating fake installations or equipment to mislead enemy intelligence assessments.
Some Counter-Deception Techniques, Adapted from Counter-Deception Planning (Chapter 62 pp 551 — 575) by William R. Harris
Reconstructive Inference
Reconstructive inference is an analytical process that involves compiling and interpreting dispersed and often misleading information to discern an adversary’s true intentions. This technique is rooted in the ability to identify and piece together "sprignals" — spurious signals that may initially appear trivial or unrelated but are in fact part of a larger, covert strategy. An illustration reconstructive inference is seen in the Allied efforts during World War II to decode encrypted communications via the Enigma machine. German forces encrypted their strategic communications using this complex cipher device, which they believed was unbreakable. Allied cryptologists, based at Bletchley Park, collected fragmented and encrypted signals intercepted from German operations. Through meticulous analysis and the development of early computers like the Bombe, they managed not only to crack the cipher but also to reconstruct the context and strategy behind the communications. This breakthrough was instrumental in several pivotal moments of the war, such as directing naval confrontations in the Atlantic and preparing for the D-Day invasion. In contemporary settings, reconstructive inference is crucial in cybersecurity and counterterrorism. Intelligence agencies collect vast amounts of digital data, often only capturing fragments of potential threats or plots. Analysts must then reconstruct the adversary’s plan from these incomplete pieces, much like assembling a jigsaw puzzle without having the picture on the box. Technologies such as machine learning and data analytics have become essential tools in this process, helping to identify patterns and connections that are not immediately obvious.
The Zimmerman Telegram (World War I)
During World War I, reconstructive inference played a crucial role in the interception and decryption of the Zimmerman Telegram. This secret diplomatic communication sent by the German Foreign Office proposed a military alliance between Germany and Mexico in the event of the United States entering the war against Germany. British cryptographers intercepted the telegram and were able to reconstruct its contents, which suggested Germany's intentions to incite war between Mexico and the U.S. This critical intelligence led to a shift in public opinion in the United States and was a significant factor in the U.S. decision to enter the war against Germany.
ISIS Communications (Syria and Iraq)
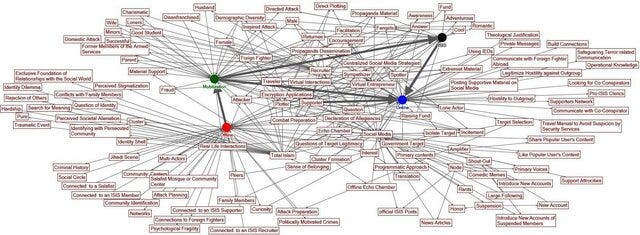
In modern conflicts, such as the ongoing issues in Syria and Iraq, reconstructive inference has been utilized to understand and counteract ISIS strategies. Intelligence agencies have gathered bits of digital communications, propaganda releases, and movement data of ISIS operatives. Through analysis, they have reconstructed ISIS's recruitment methods, financial operations, and logistical networks, enabling targeted military strikes and disruption of their operational capabilities, significantly degrading their ability to carry out attacks.
Incongruity Testing
Incongruity testing is a critical method within intelligence analysis that involves evaluating the consistency of new information with existing data. This technique is predicated on the assumption that information from reliable sources should fit within a known pattern or framework. Discrepancies or anomalies may indicate manipulation, deception, or a change in adversary behavior. In the realm of cybersecurity, incongruity testing is paramount. Security systems equipped with advanced anomaly detection capabilities continuously scan network traffic, seeking deviations from established patterns. For example, a sudden increase in data transfer at an unusual time might be flagged for further investigation. This could reveal a covert data breach attempt disguised as legitimate traffic, allowing security teams to mitigate potential threats in real-time. Another pertinent example is email phishing detection. Security software compares incoming emails against known phishing characteristics and regular communication patterns. Deviations such as suspicious attachments, mismatched URLs, or unexpected sender information trigger alerts, prompting users to exercise caution, thereby averting potential security breaches. The broader application of incongruity testing in intelligence gathering extends beyond cyber threats to international espionage and counterterrorism. Intelligence agencies employ this technique to assess the credibility of informants and the authenticity of information that could influence national security decisions. By systematically testing alternative hypotheses and checking for inconsistencies, analysts can separate deceptive information from genuine intelligence, thereby ensuring operational integrity and strategic accuracy.
Cuban Missile Crisis (1962)

During the Cuban Missile Crisis, U.S. intelligence utilized aerial photos taken by U-2 spy planes to identify Soviet missile bases under construction in Cuba. Incongruity testing was applied as analysts compared these images against known Soviet missile installations and typical deployment patterns. The discrepancies observed led to the conclusion that these were indeed offensive missile sites aimed at the U.S., leading President Kennedy to enact a naval blockade and negotiate the removal of the missiles with the Soviet Union.
Russian Activities in Eastern Europe
Currently, incongruity testing is a critical component in monitoring Russian military activities in Eastern Europe, including the conflicts in Ukraine. Western intelligence agencies analyze satellite imagery, intercepted communications, and troop movements, testing these against normal Russian military exercises and known tactics. This helps in distinguishing between ordinary military activities and potential aggressive maneuvers, such as the buildup of forces along borders or covert operations in sovereign nations.

Vulnerability Assessment
Vulnerability assessment in intelligence work involves evaluating the potential avenues through which an adversary might exploit weaknesses in security systems or national defense. This method combines historical analysis, current threat assessment, and predictive modeling to prepare for and prevent future vulnerabilities. A contemporary example of vulnerability assessment in action is observed in the strategic military deceptions employed during the Ukraine conflict with Russia, notably during the Kharkiv/Kherson operations. Ukrainian forces, with adept intelligence backing, utilized decoys and misinformation to mislead Russian military assessments regarding the real points of attack. This not only confused the adversary but also allowed Ukrainian forces to concentrate their real capabilities on strategic targets, showcasing a sophisticated application of vulnerability assessment combined with operational deception. The scientific backbone of vulnerability assessment often involves Bayesian statistics, which allow analysts to update the probability of various scenarios as new evidence becomes available. This approach is particularly useful in intelligence settings where new information continuously influences the assessment of an adversary’s next likely actions. By estimating probabilities based on accumulated historical data and current observations, intelligence agencies can effectively prepare for a range of potential enemy actions, enhancing their preemptive capabilities.
Operation Barbarossa (World War II)
A significant historical instance of vulnerability assessment occurred prior to Operation Barbarossa, Hitler’s invasion of the Soviet Union. Despite several intelligence warnings from various sources about the German buildup on the Soviet border, Stalin's analysts failed to correctly assess these vulnerabilities, partly due to preconceived notions about German intentions and the timing of the attack. This underestimation led to the initial success of the German invasion, demonstrating the consequences of inadequate vulnerability assessment.
South China Sea Tensions
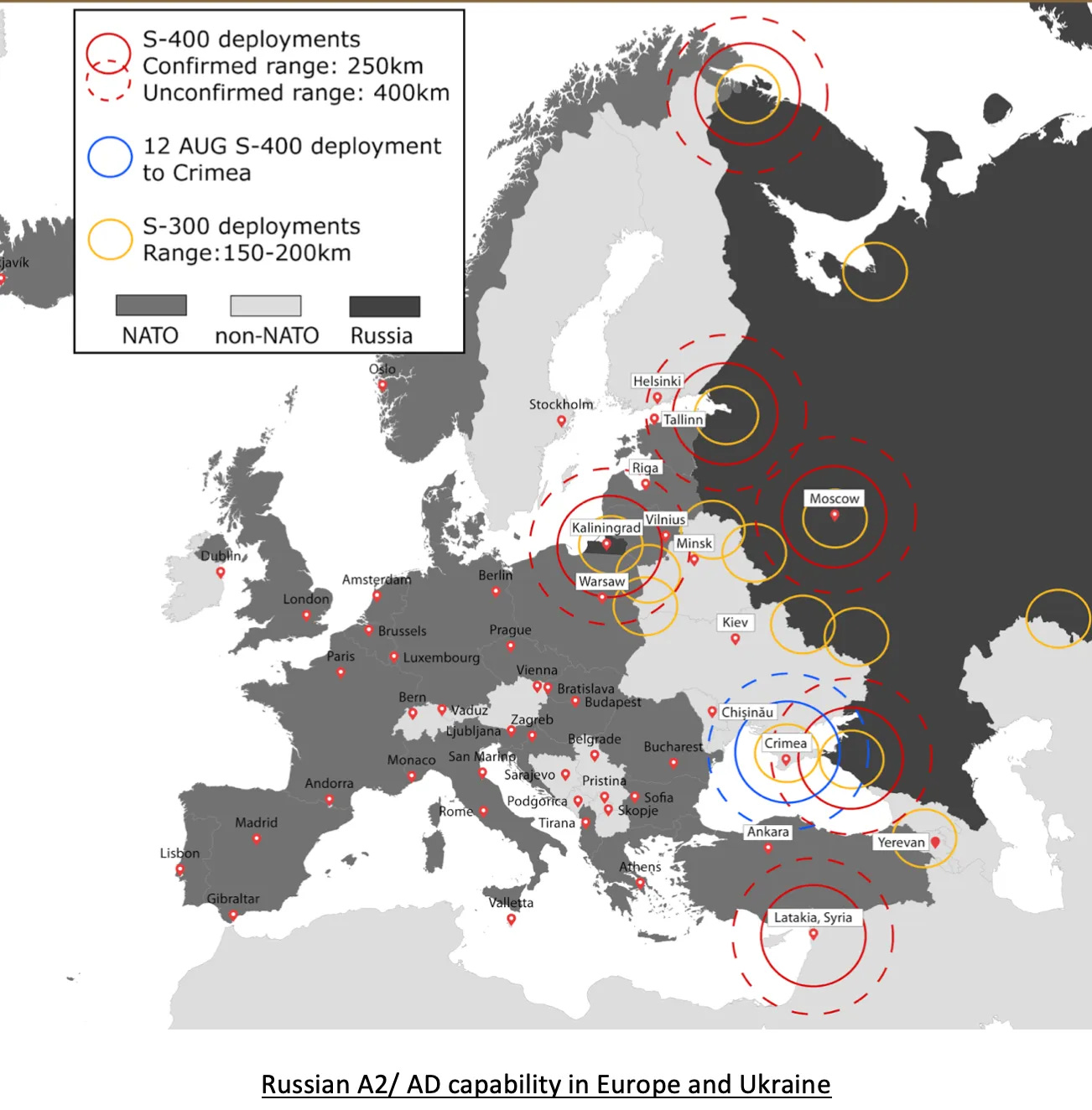
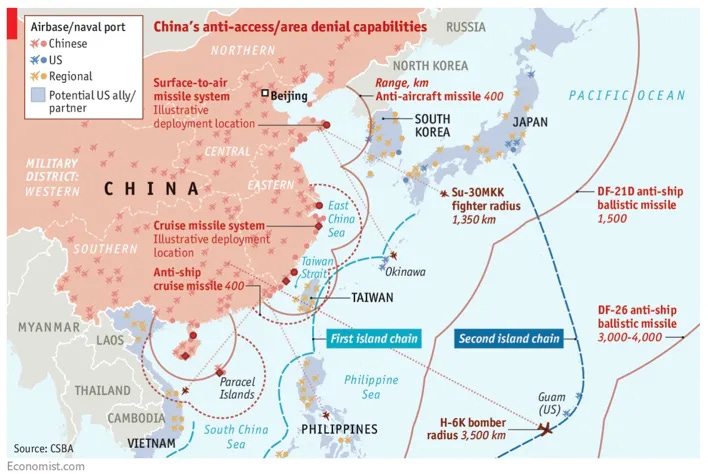
In the context of modern geopolitical tensions in the South China Sea, the U.S. and its allies continuously assess vulnerabilities in their maritime and air defense setups in the region. This involves analyzing potential Chinese military strategies, such as the deployment of anti-access/area denial (A2/AD) systems that could threaten free navigation. Through continuous vulnerability assessments, strategies are formulated to ensure that any potential military escalation by China can be effectively countered, ensuring the security of international shipping lanes and deterring unilateral territorial claims.
Concluding Remarks
As we move into modern conflicts and security threats, the role of counterintelligence and counter-deception becomes increasingly critical for analysts. The historical lessons and contemporary applications of CI show us that not only must we learn to detect deception, but we must also master the art of deception ourselves to maintain a strategic advantage and ultimately, the strength of a nation’s CI capabilities may well determine its ability to protect its national interests and maintain stability in an unpredictable global landscape.
Appendix
Sanshiro Hosaka (2022) Repeating History: Soviet Offensive Counterintelligence Active Measures, International Journal of Intelligence and CounterIntelligence, 35:3, 429-458
Filip Kovacevic (2023) “An Ominous Talent”: Oleg Gribanov and KGB Counterintelligence, International Journal of Intelligence and CounterIntelligence, 36:3, 785-815
Aden C. Magee (2024) Counterintelligence Black Swan: KGB Deception, Countersurveillance, and Active Measures Operation, International Journal of Intelligence and CounterIntelligence, 37:1, 232-264
Robin Winks, “Counterintelligence (CI) vs Counterespionage (CE),” in Cloak and Gown, New Haven: Yale University Press, 1987, pp. 421–424
Counter-Deception Planning by William R. Harris, pp. 551-575